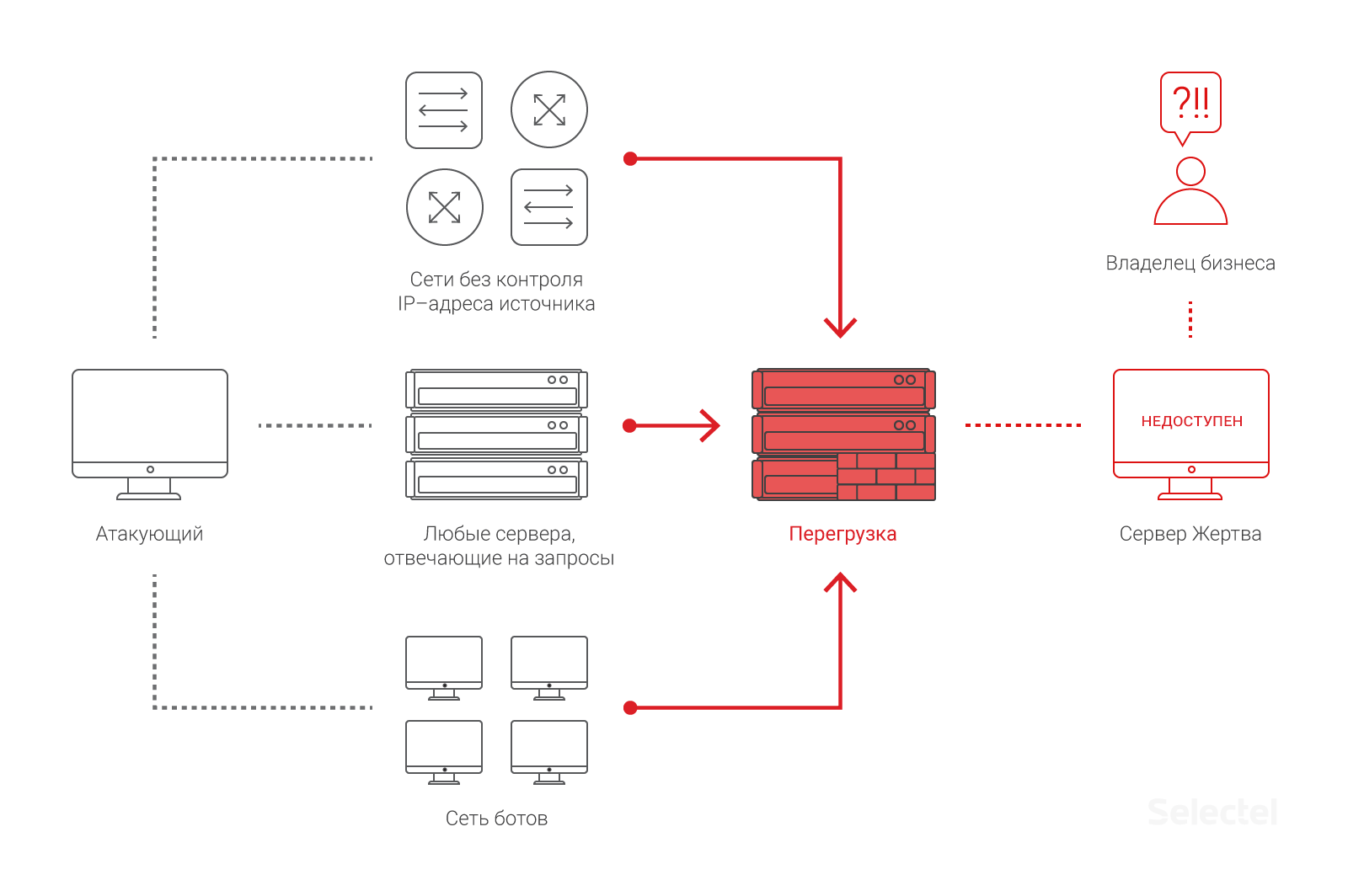
A DDoS attack - is one of the most common types of cyberattacks that aims to shut down a server, application, or network by overloading them with traffic. As a result, there is a denial of service, which can lead to serious problems for companies and organizations.
There are several types of DDoS attacks, including a network-level attack, an application-level attack, and a protocol attack. Each of these types has its own characteristics and methods of prevention.
There are several ways to protect against DDoS attacks, such as using special hardware devices, cloud solutions, CDN services, as well as properly configuring network devices and software. It is important to maintain regular updates of security measures and monitoring of network traffic.
What is a DDoS attack?
During a DDoS attack, attackers can use various methods: from attacks on server computing resources to drowning the network with data packets. The purpose of such attacks can be either money extortion or simply disruption of the service or the site.
Types of DDoS attacks
DDoS attacks can be divided into several main types:
1. Protocol-level attack
Protocol-level attacks are aimed at exhausting network-level resources, such as SYN flood, ICMP flood, and others.
2. Application-level attack
Application-level attacks purposefully distort legitimate traffic, such as attacks on HTTP, DNS, and other applications.
Type of attack Description
SYN flood is an attack in which an attacker sends a large number of SYN packets to exhaust server resources.
ICMP flood Attacker sends a lot of ICMP packets to overload the network.
HTTP flood is an attack in which an attacker sends multiple HTTP requests to overload a web server.
DDoS Detection Methods
1. Monitoring anomalies in network traffic Monitoring network traffic and identifying unusual patterns of data flows may indicate the possible presence of a DDoS attack.
2. Analyzing user behavior Checking for unusual or abnormal user behavior on a web resource can help identify potential DDoS attacks.
3. Monitoring network and server performance Monitoring network resources, its load and server performance helps to identify abnormal changes that may indicate DDoS.
DDoS protection methods
There are various methods of protection against DDoS attacks that help reduce the negative impact on a website or online service. Some of the main ways to protect yourself include:
Traffic filtering
One of the effective methods of DDoS protection is traffic filtering. This allows you to filter out malicious traffic by blocking requests from suspicious sources.
Using a CDN
The Content Delivery Network (CDN) is a network of servers distributed around the world that can handle user requests. Using CDN allows you to distribute the load and protect the site from DDoS attacks.
Configuring firewalls
Using cloud-based security solutions
Internetwork grouping (IP Spoofing)
The choice of a specific protection method should depend on the characteristics and potential vulnerability of your web resource.
Security software
There are many software products designed to protect against DDoS attacks. These programs can detect abnormal traffic and block it before it damages the server.
Cloudflare
One of the most popular tools to protect against DDoS attacks. Cloudflare offers high speed and a high level of protection, thanks to a distributed network of servers around the world.
Incapsula
Another popular cloud-based solution to protect against DDoS attacks. Incapsula provides reliable protection and convenient monitoring tools.
Recommendations for DDoS prevention
To protect against DDoS attacks, there are several basic recommendations that will help reduce the risk of this type of attack:
1. Using specialized DDoS protection solutions
It is important to have security tools in place that are specialized in detecting and blocking DDoS attacks. This allows you to quickly respond to attacks and minimize their impact on the system.
2. Setting up load balancing
Evenly distributing traffic between different servers or resources can reduce the likelihood of a successful DDoS attack. Load balancing allows you to reduce the vulnerability of the system to attacks by unloading individual nodes.
The software and drivers used should be regularly updated and monitored;
It is necessary to set up network monitoring to detect abnormal traffic in a timely manner;
It is recommended to connect filters to the system to block known sources of DDoS attacks;
Compliance with security recommendations when working with the network and servers;
Question and answer:
DDoS
(Distributed Denial of Service) attack is a method of attacking a computer system, which consists in the fact that an attacker creates a large amount of network traffic and directs it to a target, which leads to resource overload and inability to access services.
What types of DDoS attacks exist?
There are several types of DDoS attacks, including Application Layer DDoS attacks, Transport Layer DDoS attacks, and Network Layer DDoS attacks.
What are the ways to protect against DDoS attacks?
There are several ways to protect against DDoS attacks, such as using CDN (Content Delivery Network) services, blocking the attacker's IP addresses, configuring a firewall to filter traffic, using anti-DDoS services, etc.
How can attackers find out information about the weaknesses of your system for a DDoS attack?
Attackers can use various tools to scan and identify vulnerabilities in your system, such as vulnerability scanners, searching for open ports, etc. Social engineering and information leaks can also be used.